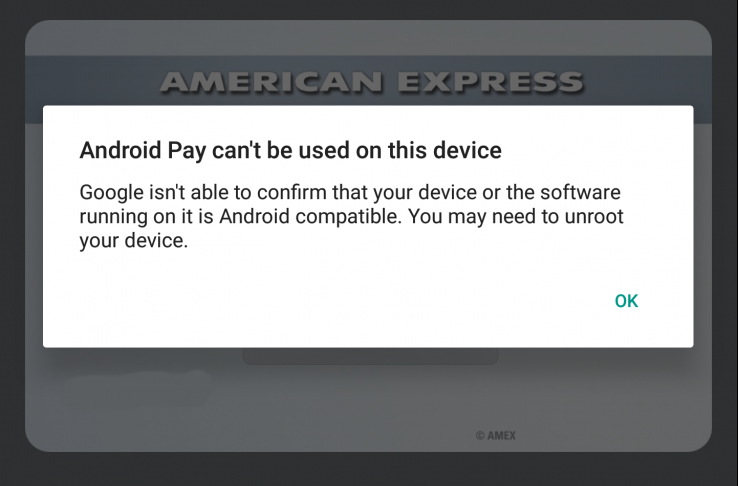
It's Bad News Wednesday for developers and power users alike. A pleasant day was punctured by several reports coming in that a new update to Android's SafetyNet not only caused existing su hiding mechanisms to stop working (normal case scenario), but also started giving adverse results on devices which were not even rooted!
 Initiating from Reddit's Nexus 6P forums, and then being echoed around at several places including the Reddit Android forums, our own Nexus 6P forums and threads for suhide and Magisk, users are finding that the latest update to SafetyNet is causing devices to fail checks if they have an unlocked bootloader. Users have tried out different combinations of modification scenarios and masking methods, but the common factor for failure in most cases boils down to the bootloader being unlocked.
Initiating from Reddit's Nexus 6P forums, and then being echoed around at several places including the Reddit Android forums, our own Nexus 6P forums and threads for suhide and Magisk, users are finding that the latest update to SafetyNet is causing devices to fail checks if they have an unlocked bootloader. Users have tried out different combinations of modification scenarios and masking methods, but the common factor for failure in most cases boils down to the bootloader being unlocked.
Unlocking the bootloader is the first step for unofficial modifications for most devices. If the latest SafetyNet update does indeed check for the bootloader status, this might mean the end of the days where one could run Android Pay and other SafetyNet based apps in conjunction with root and Xposed by employing masking techniques.
Magisk developer topjohnwu commented on the early situation, pointing that SafetyNet might be a lost cause after this update:
"Keep in mind, in the latest update of Safety Net that just happened in a few hours, Google seems to step up the game, and it might got to the point that no modifications are allowed, and might be impossible to bypass.
Currently on my HTC 10, no matter what I did to the boot image, even just a repack of 100% stock boot image, Safety Net will not pass under any circumstances. On the other hand, my Nexus 9 running stock Nougat seems bypass without issues, with root and modules all enabled and working fine. The boot verification might vary from one OEM to another, HTC's implementation might just be one of the first included into Safety Net, but eventually all major OEMs' method will be included, and at that time I think any Android "mod", including custom kernels, will pretty much break Safety Net. These verification should be coded deep into the bootloader, which is not that easy to crack. So the conclusion is that I will not spend that much time bypassing Safety Net in the future."
Back when suhide was released, Chainfire had predicted something along the same lines:
Ultimately, information will be provided and verified by bootloaders/TrustZone/SecureBoot/TIMA/TEE/TPM etc. (Samsung is already doing this with their KNOX/TIMA solutions). Parts of the device we cannot easily reach or patch, and thus there will come a time when these detection bypasses may no longer [be] viable.
Since the situation is still developing, things might be more complex than what they appear on the surface. We will keep our readers posted if there are new developments on the matter.