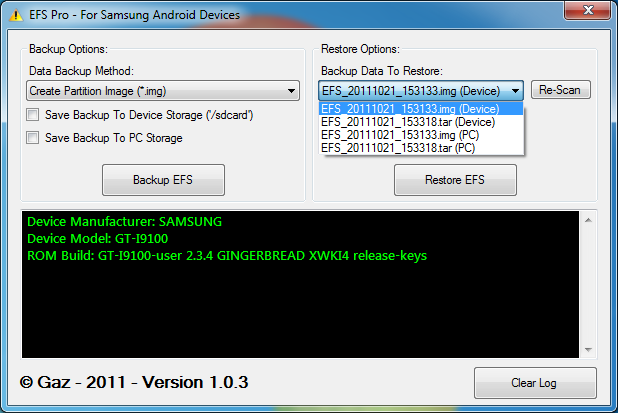
The wonderful world of NV, EFS, and all the inherent dangers that come from messing with this. For those of you who have no clue as to what I am talking about, there is a dark, really deep and well protected section of your device that is virtually immune to any kind of flashing and manipulation (unless of course you know how to access it). This part of the device contains information such as IMEI (or MEID and ESN in the case of CDMA devices), programming parameters for the device such as your account information (phone number, etc), data provisioning parameters, and a whole bunch of other things that, when not handled properly, can render a device completely useless. All of these are contained in the infamous \EFS folder. XDA Recognized Developer lyriquidperfection just updated an app that he started working on not too long ago, which basically allows you to back up and restore the contents of this folder, just in case. It seems to be rather simple to corrupt this by trying to unlock or change certain "numbers" in it, which is why being able to back up the original thing is rather important. HTC devices are normally associated with tweaking this due to the ease of getting the device in Diag mode via EPST. However, Samsung devices (and really most devices out there) can indeed be put in Diag mode to access this special section.
Before you go digging around for ways to mess with your EFS folder, you need to understand that, unlike flashing a device (which could potentially lead to bricks as well) could render your device completely useless as it will no longer be recognized by your carrier. From this point, there is no tool to allow you to recover from a mistake done in here, so proceed with extreme caution. Have fun and happy (and safe) hacking!
This is a very sensitive system folder that contains Phone-specific information such as the IMEI (encrypted in the nv_data.bin), wireless devices MAC addresses, product code (also in the nv_data.bin), and much more. Often users trying to change product codes or trying to unlock the mobile will end up corrupting data in this location.
You can find more information in the original thread.
Want something published in the Portal? Contact any News Writer.
Thanks lyriquidperfection for the tip!