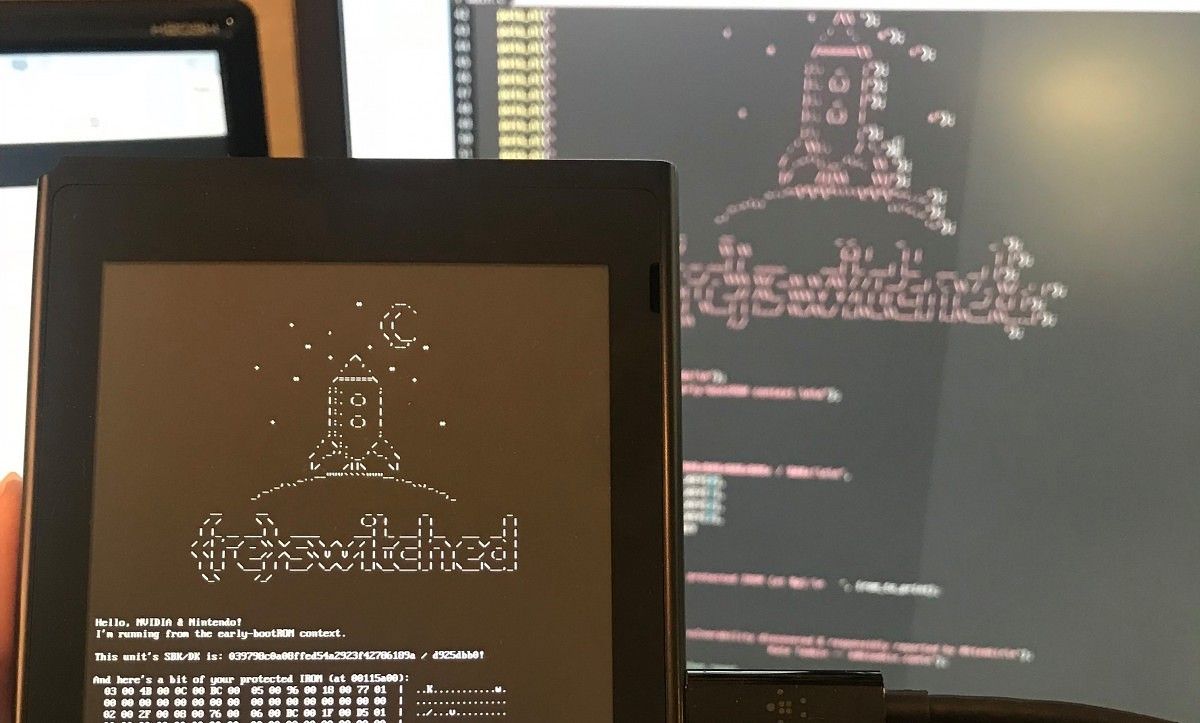
If you're a gamer, you may have heard the incredible news out yesterday about the Nintendo Switch: It has been cracked wide open. A new vulnerability in the Nvidia Tegra X1, the system-on-chip found in the Nintendo Switch but also devices like the Google Pixel C and Nvidia Shield Android TV, has been discovered. The vulnerability, called Fusée Gelée, was discovered by Katherine Temkin in collaboration with ReSwitched, a hacking team dedicated to opening up the Switch for homebrew access. During the course of their work, they found a vulnerability that achieves exactly what they were looking for, but because of its platform-specificity, affects more devices than they probably intended.
I won't pretend to be able to fully describe the vulnerability in detail, but the basic explanation is that Nvidia Tegra SoCs released before the T186/X2 are susceptible to an attack via the USB software stack that allows for arbitrary code execution on the device. In particular, the exploit takes advantage of sending a specially constructed USB copy operation (whose length is controlled by the attacker) to gain control of the "Boot and Power Management processor" to then load any arbitrary code onto the main application processors at the highest privilege possible.
Since the bug is in the Boot ROM, it cannot be patched without a hardware revision at the factory. That means all devices with the aforementioned Tegra system-on-chips are vulnerable, and no software update will be able to patch it. Luckily, it requires physical access to the device to exploit, so your device is safe so long as an attacker can't get access in-person. Security issues aside, this discovery has the gaming community abuzz because of its implications for Nintendo Switch homebrew (and let's be honest here, for piracy.) But as we aren't a gaming forum, let's discuss some of the other implications of this finding.
Android on Switch? Custom Bootloaders for Shield devices? What Fusée Gelée could mean for us.
As the vulnerability was originally intended for disclosure on June 15th, 2018, the team of developers working on it have not had much time to fully put it to use. We expect several modifications to be made available in the coming days and weeks. As a teaser, the guys over at fail0verflow have tested getting a GNU/Linux distribution running on the Nintendo Switch, as shown below.
In the future, it may be possible to get even Android up and running on the Nintendo Switch. We could be running LineageOS 15.1 on it if enough developers cared for it (and the Switch certainly has a dedicated user base). It's too early to say for sure, but given that the SoC is already in use for really popular and well-documented Android devices (Pixel C and Nvidia Shield), I'm guessing it's more likely than not it'll happen.
As for existing Android devices with the Tegra X1 SoC, there's a lot to look forward to. Sure, devices like the Pixel C and Shield already have a thriving developer community, but the level of device access provided by this exploit will be unprecedented. According to LineageOS developer and XDA Senior Member npjohnson, developers can start building a custom bootloader such as one based on UEFI (and even something like EFIDroid for native multiboot), modify the Trusted Execution Environment (TEE) to allow for Widevine L1 or OMX secure decoding on devices that don't support it, blowing fuses and then reading them, falsifying lock status, and much more.
This critical Tegra X1 vulnerability has a lot to offer for developers looking to exploit it, so we'll have to wait and see what people are able to cook up. Still, a vulnerability is a vulnerability, so if you are worried that someone might use it to steal your data, it's probably best to change devices because there's no fix coming for this issue.