Update 10/10/19 @ 3:05 AM ET: The zero-day Android vulnerability has been patched with the October 6, 2019 security patch. Scroll to the bottom for more information. The article as published on October 6, 2019, is preserved as below.
Security has been one of the top priorities in recent Android updates, with improvements and changes to encryption, permissions, and privacy-related handling being some of the headlining features. Other initiatives such as Project Mainline for Android 10 aim at speeding up security updates in order to make Android devices safer. Google has also been diligent and punctual with security patches, and while these efforts are commendable in their own right, there will always remain scope for exploits and vulnerabilities in an OS like Android. As it turns out, attackers have been allegedly found actively exploiting a zero-day vulnerability in Android that allows them to take over full control of certain phones from Google, Huawei, Xiaomi, Samsung and others.
Google's Project Zero team has revealed information about a zero-day Android exploit, the active use of which is being attributed to the NSO group, though representatives from NSO have denied the use of the same to ArsTechnica. This exploit is a kernel privilege escalation that uses a use-after-free vulnerability, allowing the attacker to fully compromise a vulnerable device and root it. Since the exploit is also accessible from the Chrome sandbox, it can also be delivered via the web once it is paired with an exploit that targets a vulnerability in the code in Chrome that is used to render content.
In simpler language, an attacker can install a malicious application on affected devices and achieve root without the user's knowledge, and as we all know, the road opens up completely after that. And since it can be chained with another exploit in the Chrome browser, the attacker can also deliver the malicious application through the web browser, removing the need for physical access to the device. If this sounds serious to you, then that is because it certainly is -- the vulnerability has been rated as "High Severity" on Android. What's worse, this exploit requires little to no per-device customization, and the researchers at Project Zero also have proof of the exploit being used in the wild.
The vulnerability was apparently patched in December 2017 in the Linux Kernel 4.14 LTS release but without a tracking CVE. The fix was then incorporated into versions 3.18, 4.4, and 4.9 of the Android kernel. However, the fix did not make its way into Android security updates, leaving several devices vulnerable to this flaw that is now being tracked as CVE-2019-2215.
The "non-exhaustive" list of devices that have been found to be affected are as follows:
- Google Pixel
- Google Pixel XL
- Google Pixel 2
- Google Pixel 2 XL
- Huawei P20
- Xiaomi Redmi 5A
- Xiaomi Redmi Note 5
- Xiaomi Mi A1
- Oppo A3
- Moto Z3
- LG phones on Android Oreo
- Samsung Galaxy S7
- Samsung Galaxy S8
- Samsung Galaxy S9
However, as mentioned, this is not an exhaustive list, which means that several other devices are also likely to have been affected by this vulnerability despite having Android security updates as new as the one from September 2019. The Google Pixel 3 and Pixel 3 XL and Google Pixel 3a and Pixel 3a XL are said to be safe from this vulnerability. Affected Pixel devices will have the vulnerability patched in the upcoming October 2019 Android security update, which should go live in a day or two. A patch has been made available to Android partners "in order to ensure the Android ecosystem is protected against the issue", but seeing how careless and nonchalant certain OEMs are about updates, we wouldn't hold our breaths on receiving the fix in a timely manner.
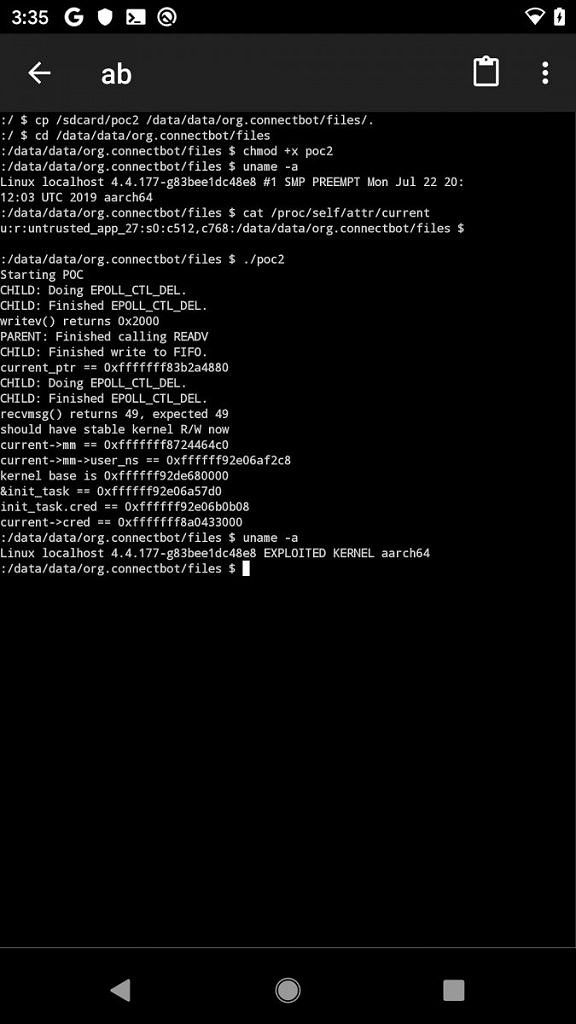
The Project Zero research team has shared a local proof-of-concept exploit to demonstrate how this bug can be used to gain arbitrary kernel read/write when running locally.
The Project Zero research team has promised to provide a more detailed explanation of the bug and the methodology to identify it in a future blog post. ArsTechnica is of the opinion that there are extremely slim chances of being exploited by attacks as expensive and targeted as this one; and that users should still hold off on installing non-essential apps and use a non-Chrome browser until the patch is installed. In our opinion, we would add that it would also be prudent to look out for the October 2019 security patch for your device and install it as soon as possible.
Source: Project Zero
Story Via: ArsTechnica
Update: The Zero-day Android vulnerability has been patched with the October 2019 security update
CVE-2019-2215 which relates to the above-mentioned kernel privilege escalation vulnerability has been patched with the October 2019 security patch, specifically with security patch level 2019-10-06, as promised. If a security update is available for your device, we highly recommend installing it at the earliest.
Source: Android Security Bulletin