Researchers at Check Point have discovered new malware hidden in about 60 games and applications on the Google Play Store. It's dubbed "AdultSwine", and it displays pornographic advertisements, entices users to install fake security applications, and tries to make users sign up for premium services.
The infected apps, which are mostly aimed at children, have been downloaded between three million and seven million times, according to Google Play Store download statistics.
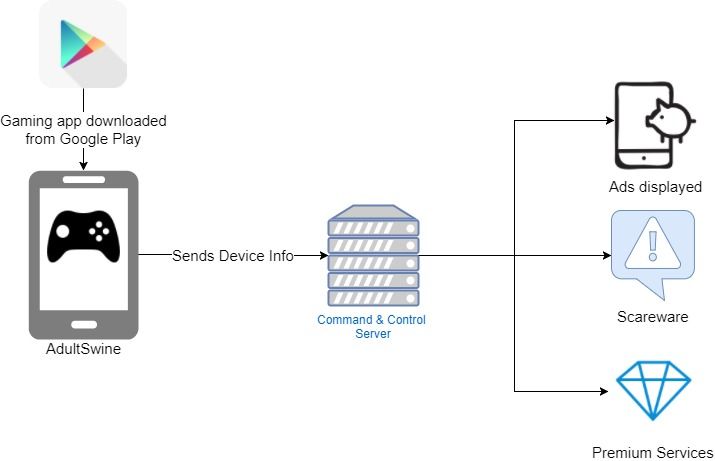
How AdultSwine Works
AdultSwine works in a fairly straightforward way. Once the user downloads and installs an affected app and launches it for the first time, the malware begins to send device info to a command and control server. The server sends configuration files tailored to the infected phone or tablet, which in turn determine the operations the malware can perform.
AdultSwine Displays Pornographic and Inappropriate Advertisements
The primary goal of AdultSwine is to make its creators money, and one way it accomplishes that is by displaying pornographic and other inappropriate advertisements. The command and control server determines which ads are displayed and when, and it keeps the malware active even when the user switches to another, uninfected app by injecting advertisements where possible.
Once online, AdultSwine checks which applications are running and where it can inject advertisements. It displays ads from two different networks: One legitimate (but annoying) one, and a second one created specifically for AdultSwine that contains a host of inappropriate and pornographic ads. These ads are presented to users regardless of their ages or browsing habits.
AdultSwine has an interesting self-preservation method it uses to avoid detection: It doesn't inject ads into applications such as browsers social networks, where they're likely to be more conspicuous.
AdultSwine Uses Scareware Tactics to Entice Users to Install "Security" Applications
AdultSwine's other tactic is to entice users to install "security" applications by claiming that their device is infected, and by "recommending" apps can remove the virus for them. In one instance, researchers at Check Point were redirected to install a browser which would allegedly remove a "virus".
It might seem like an obvious example of scareware -- the browser in question didn't actually remove viruses. But the target audience -- kids -- might not be able to tell.
AdultSwine Tries to Register Users with Premium Services
In yet another scheme designed to exploit children, the AdultSwine tries to register users for premium-rate services. It displays advertisements which the users have to click, and once they do, those ads tell users they can win a free iPhone by answering four questions. After answering those questions, it gives users the option of claiming the free iPhone by entering their phone number. But there's no iPhone -- instead, the phone number is used to sign up for premium services.
AdultSwine Could be Much Worse, But It's Still Pretty Bad
While we have seen malware capable of doing much more damage in the past, AdultSwine isn't any better. It clearly has a different agenda, but it's just as malicious in nature and should be uninstalled as soon as possible.
Here's a list of all applications known to be infected by AdultSwine:
You can read the original report at the source link.
Update 1/13/2018: Google has removed apps affected by AdultSwine from the Play Store, according to Reuters. “We’ve removed the apps from Play, disabled the developers’ accounts, and will continue to show strong warnings to anyone that has installed them,” a Google spokesperson told the publication.