Memory safety has been a major priority for Google lately, as memory safety bugs tend to be some of the most severe bugs in software development. In fact, memory safety vulnerabilities used to account for a majority of severe Android vulnerabilities until 2022, which is when Google wrote a significant portion of Android’s new native code in the Rust programming language instead of C/C++. Google has been working on supporting other means to mitigate memory safety vulnerabilities in Android, one of which is called memory tagging. On supported devices running Android 14, there may be a new “advanced memory protection” setting that could toggle this feature.
Memory Tagging Extension (MTE) is a mandatory hardware feature of Arm v9 CPUs that protects against memory safety bugs (with a slight runtime performance cost overhead) by providing detailed information about memory violations. As Google explains, “at a high level, MTE tags each memory allocation/deallocation with additional metadata. It assigns a tag to a memory location, which can then be associated with pointers that reference that memory location. At runtime the CPU checks that the pointer and the metadata tags match on each load and store.”
Google has been working to support MTE throughout the Android software stack for several releases now. In Android 12, scudo, Android’s heap allocator, added support for three MTE operating modes on compatible devices: synchronous mode, asynchronous mode, and asymmetric mode. Google also made it possible to enable MTE for system processes at build time or through system properties and/or environment variables. Applications can opt-in to supporting MTE through the android:memtagMode attribute. When MTE is enabled for processes in Android, entire classes of memory safety bugs such as use-after-free and buffer overflows trigger a crash instead of a silent memory corruption.
In Android 13, Google added an ABI for the userspace to communicate the requested MTE operating mode to the bootloader. This could be used to enable MTE on compatible devices that do not ship with it enabled by default, or alternatively it could be used to disable it on compatible devices that do have it enabled by default. Setting the ro.arm64.memtag.bootctl_supported system property to “true” in Android 13 would tell the system that the bootloader supports the ABI and also trigger a button to appear in the Developer Options menu that allowed the user to enable MTE on the next reboot. This was aimed at developers who wanted to test the behavior of their apps with MTE enabled.
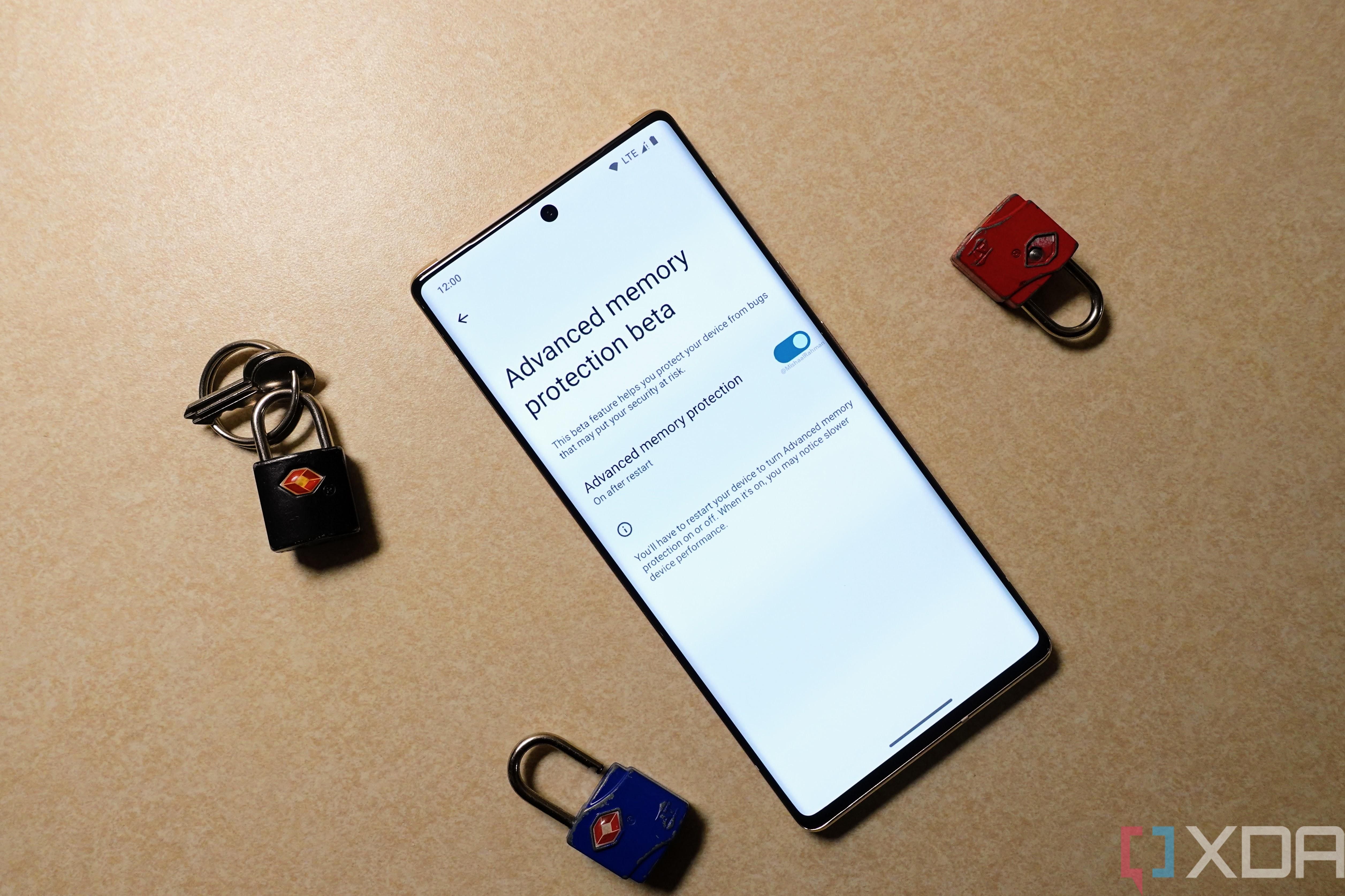
In Android 14, though, enabling MTE on compatible devices may longer require diving into Developer Options. If the device features an Arm v8.5+ CPU with MTE support, the device implementation supports the ABI for communicating the requested MTE operating mode to the bootloader, and the new system property ‘ro.arm64.memtag.bootctl_settings_toggle’ is set to true, then a new “advanced memory protection” page may appear in Settings > Security & privacy > More security settings. This page can also be launched through the new ACTION_ADVANCED_MEMORY_PROTECTION_SETTINGS intent action.
Notably, the Tensor G2 chipset in the Google Pixel 7 series uses Arm v8.2 CPU cores, hence they don’t support MTE. If the upcoming Google Pixel 8 series uses new Arm v9 CPU cores like many other flagship Android devices do, then they would have hardware capable of supporting MTE. It remains to be seen if this "advanced memory protection" feature will actually make it into the stable release, however.
Thanks to security researcher @flawedworlddev for their assistance on this article!