Latest Articles
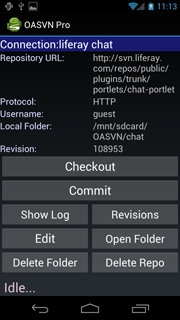
A long, long time ago, in a Portal post far away, we once covered a topic regarding a SVN guide by XDA Recognized Developer LiquidSolstice. Since then, this wonderful tool fell into darkness mainly due to the availability of things such as repos, nighties, and many other apps (e.g. Goo Manager) available from our devs, which somewhat satisfy the urge to get new builds faster. Having said that, SVN never really stopped being a useful tool for those devs who wanted to use it, mainly due to the speed and ease of use---once you get it going, that is.
There are several small PC kits for people to have computing power in the palm of their hands. Many of these are actually, low powered devices usually loaded with Android or some kind of Linux distro, whose sole purpose of existing is to---well, we are still not sure about that one, but it certainly fills a size gap in between laptops and tablets. That said, not a single one of these ultra-micro-small PC kits compare in popularity to the infamous and nearly impossible to get Raspberry Pi. In fact, just yesterday we gave the device its own home here on XDA.
So, you got your new shiny, slim, and Intel-loaded Motorola RAZR i, and could not be more grateful to Motorola for allowing you to unlock your bootloader simply simply handing them your soul warranty. Your device is now ready to flash anything that comes across your screen, be it a kernel or a ROM. However, not too many devs have purchased the device yet, and as a result, not too many ROMs are available. So, you are stuck with stock. However, thanks to having the bootloader unlocked, you can get your device rooted for all your root-requesting apps needs.
Quick, simple, and dirty. Some of the best hacks around on XDA require very little to get them to work, and make your life easier in the process. Also, these "simple tricks" tend to fix major snafus from some manufacturers when it comes to so-called features that make you ask "What in the world were they thinking?" So is the case for many Samsung Galaxy devices.
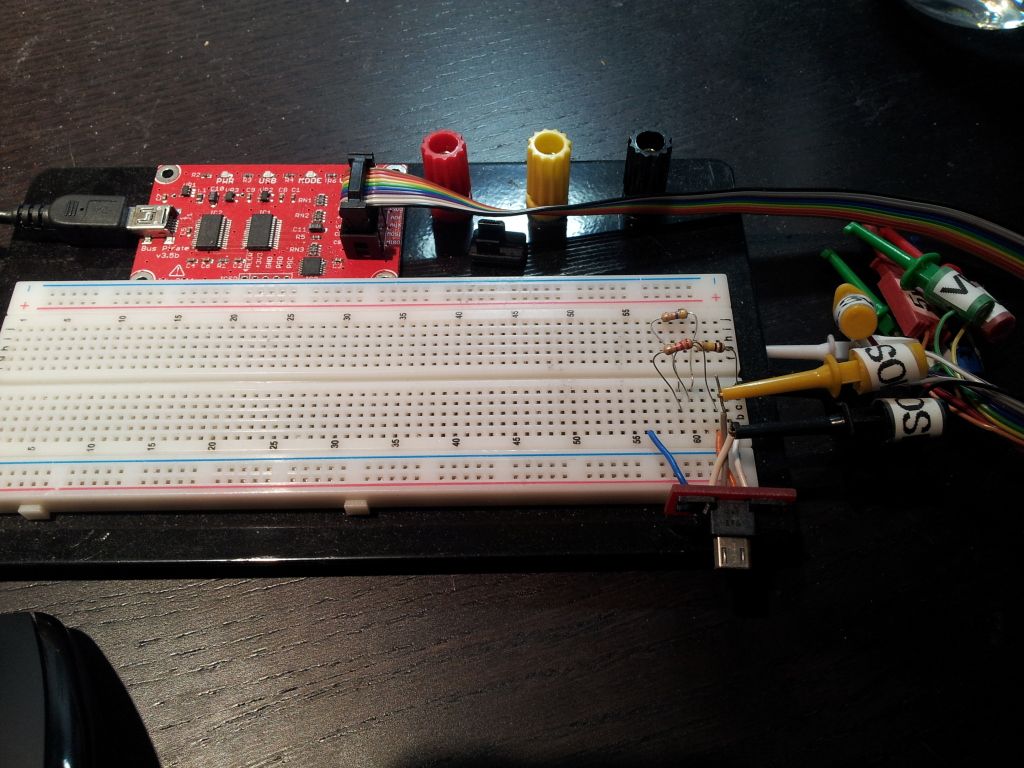
Once upon a time, a white knight in shinning armor by the name of XDA Elite Recognized Developer AdamOutler brought us tons upon tons of knowledge on hardware specifications for the Samsung Galaxy Captivate and a few other related devices. He and a few other devs like XDA Forum Member TheBeano and Recognized Developer UberPinguin also brought us the key to opening up an door for hardware mischief, and in turn revealed an entire world of possibilities for aspiring devs and end users alike. Not every device is the same, and certainly setting up UART can have its set of complications, including but not limited to, messing your device up to the point of no return (also known as completely bricking it).
One of the most important and vulnerable parts of our devices is the connection port. Be it proprietary or through USB, it not only serves the very important purpose of allowing us to gain root, sync, and transfer files to and from our PC, but it also (in most cases anyways) allows you to charge the device. As time goes by, the ports themselves may start to "lose grip" simply because of all the mechanical strain of pushing the connector in and pulling it out afterwards. When you buy a new device, it may actually be hard to unplug the connector, but it gets quite easier after some time. After the some more time has passed, the connector may not be able to hold the cable in place anymore. If this sounds like something you are going through, XDA Forum Member telmosousa has posted a guide which may help you with your issue.

Please note that the following is an addition to the infamous PDroid, developer by XDA Forum Member svyat back in December 2011. As its name clearly suggests, PDroidAddon acts along side (and will interact with) PDroid, which was basically a security suite that allowed you to "cherry pick" which apps get access to your personal information. Today, we have XDA Forum Member CollegeDev bringing us an interesting alternative that handles privacy in a different manner, or at least it targets a different source of "leaks."
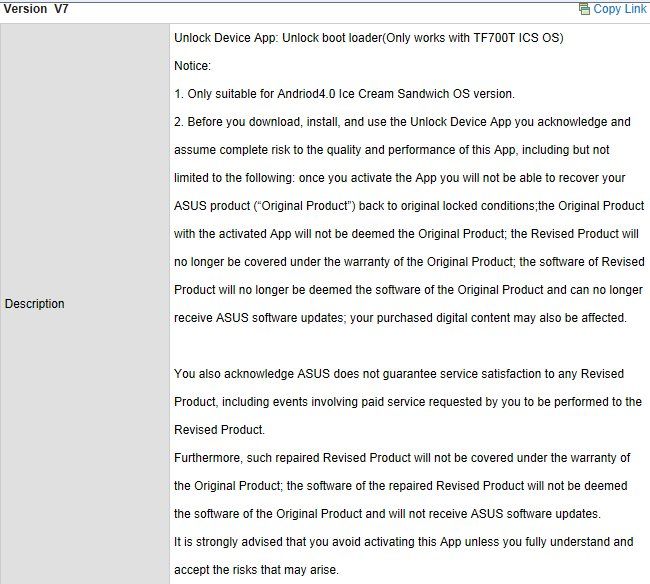
Not too long ago, we witnessed the launch of Asus most recent entry into the world of tablets with the shinny, slim, and fully loaded Infinity Pad (a.k.a. the Asus Transformer TF700T). As is customary for Asus, the bootloader on the device was locked upon shipping from the factory. However due to the constant demands, petitions, and bashing from the developer community in similar cases with the Prime (TF201) and the TF300T, they have now released an official tool to unlock the bootloader of the device.
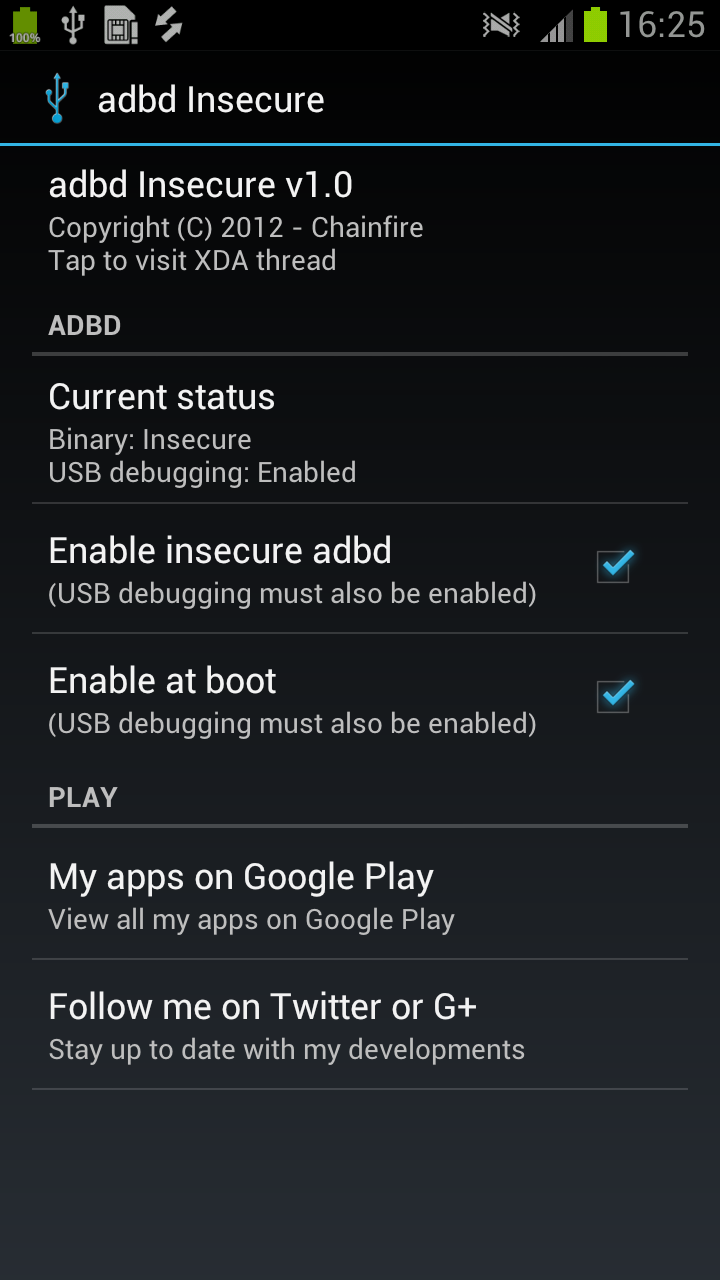
We are all undoubtedly aware of adb. In fact, most of us use it quite often in order to execute commands on our mobile devices from the comfort of our computers. It allows you to do this such as push and pull files on the device, retrieve logcats to send to your favorite dev when your kernel causes a bootloop, reboot to recovery or bootloader, and many other useful things. It is also the core of most one-click root methods. Ultimately, it is the adbd (ADB Daemon) that is responsible for allowing you to access the shell and all the other cool functions. For most stock kernels, however, it seems that this only allows you to run adb in secure mode even if you have a rooted device.

Since the latest leaks for the Samsung Galaxy S2 line up have been hitting us left and right, people have been jumping between ROMs---mainly between buggy, pre-release ICS builds and very stable GB. This is, after all, what we do on XDA as a habit: We see a leak, we flash it, we use it, and we tweak it. If it doesn't fly, we simply roll back. Of course, there is always an inherent risk in flashing stuff that should not be on your device in the first place, but the risk of fully bricking a device in this day and age is rather small. Especially, since there are tools available to bring your devices back from the dead, such as UnBrickable Mod by XDA Elite Recognized Developer AdamOutler.

About a month or so ago, XDA Forum Member biktor_gj posted an entire unlock and NAND access method for the Nokia Lumia 800 and 710 series of devices, which are the next of kin in Nokia's entry into the world of smartphones (being hand held by Microsoft themselves). The complete unlock was accomplished thanks to the collaboration of several devs including XDA Recognized Developer ultrashot. Well, the best thing about having our devices completely unlocked is that it allows them to receive and accept unsigned code such as---oh, I don't know---custom ROMs!
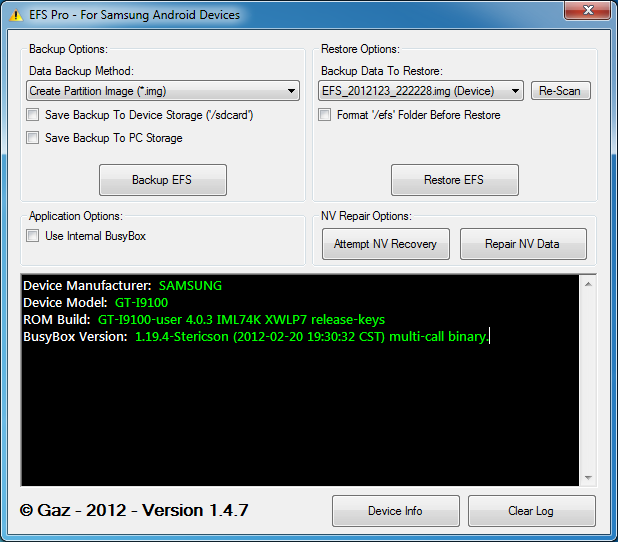
A few months back, we wrote an article about a certain app that allowed Samsung device owners to back up and restore their EFS folders, brought to you by XDA Recognized Developer lyriquidperfection. Well, it seems that the dev has been hard at work, tweaking and perfecting his tool in order to bring forth EFS Pro, which is essentially a newer, more complete and capable version of its predecessor.
Ultimate control over our devices is what we all struggle to obtain here on XDA-Developers. Microsoft has done an amazing job in making sure that this does not happen for owners of Windows Phone 7 devices (some of them anyways) by implementing security measure on top of security measure, and all this in the name of data privacy, protection to the end user, and protection of IP. This is likely one of the reasons why this platform never really got off the ground. Old time WM users will agree that playing with the registry to unlock functions (802.11g on the HTC Wizard anyone?) and to improve the overall feeling over the device and control is what probably kept WM alive and well for as long as it did. On WP7, all that was lost.
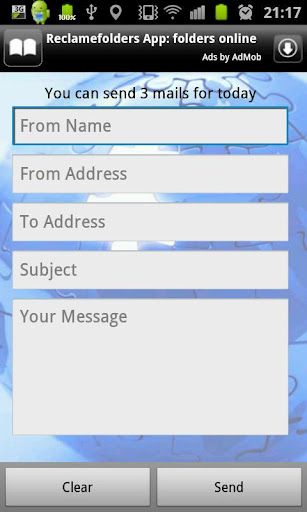
With April 1st quickly approaching us, we can't help but to start thinking about the different kind of pranks that we could potentially pull on friends, loved ones, or complete strangers (no one is exempt). Due to the large influence of electronic media and mass communication, we turn to alternatives like e-mails and such. But, how would one get around using a personal e-mail? Sure, making a new account would work wonders, but having to create it is a process that could take time out of your busy day (even if it is only 5 minutes or so). So, in the search of providing you with the needed tools for this epic day, we came across Fake Mailer by XDA Forum Member Rednasman.
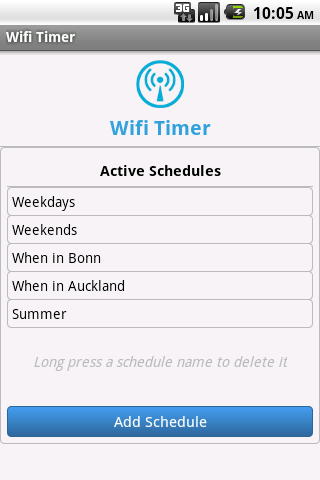
As most of you know, WiFi on most Android devices is the preferred method for connectivity for a slew of reasons: it is faster, more secure, and best of all, it uses less battery due to this being more efficient when it comes to power management. However, unless you live in a city fully covered with a WiFi signal, it is unlikely that you will want to have your device looking for a network when you know you don't have one around. This is simply a waste of your battery. How would you like to solve that without manually having to activate and deactivate your WiFi?
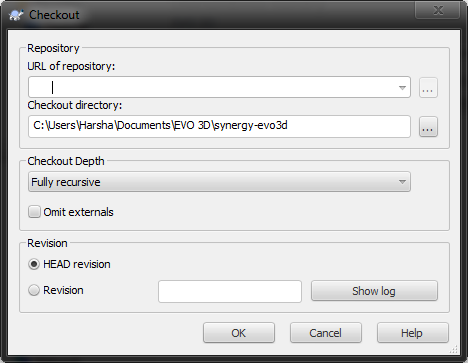
Flashing, upgrading, and more flashing. This is what most people at xda do to try and keep up with the times. This is almost a full time job/hobby for some people and sometimes, not even the devs can put out roms fast enough. Because of this, there are ways to provide junkies or ORD addicts with a faster fix. SVN, which really stands for subversion is a command that allows updates of software giving you the opportunity to easily roll back and update without any major difficulties. Basically, using SVN would allow anyone to update the builds directly from the developer's repo. The advantage of this is that you will not have to download a full new build every time as this will allow you to simply update the builds every time with whatever changes the dev may have made from the previous one. This works great for people who release nighties. If you are curious as to how this is done, XDA Recognized Developer LiquidSolstice has put out a fantastic guide, which is in essence fool proof to get this up and running in no time. The guide is complete with explanations, examples, links to files and programs, and even a full list of repos from devs present in the EVO 3D area. However, this is universal enough to be used with any dev that works with a SVN server.
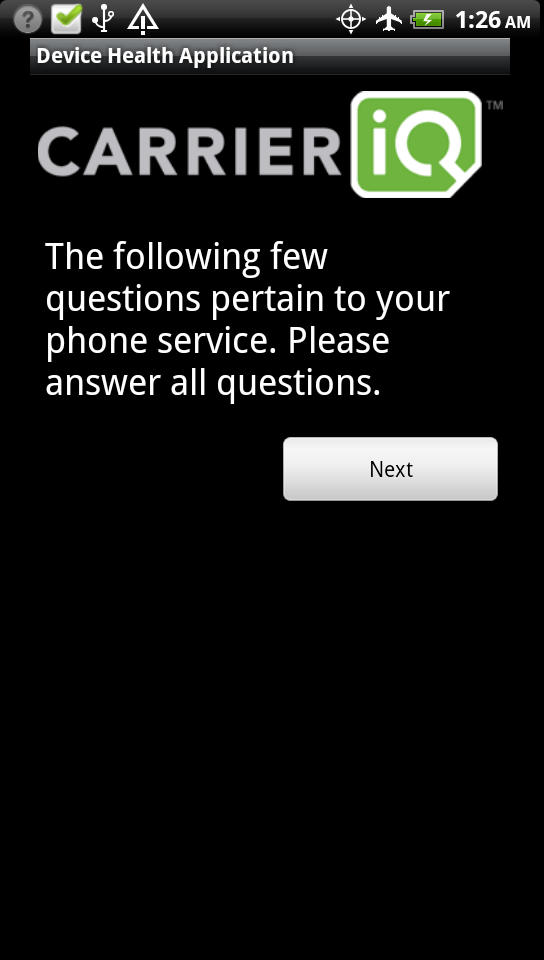
And the spy and invasion of privacy saga continues, but this time XDA Recognized Developer TrevE seems to have hit the very core of most of what is happening with devices. You may recall from a few articles back that we started talking about something called CIQ or Carrier iQ. This is, essentially, a piece of software that is embedded into most mobile devices, not just Android but Nokia, Blackberry, and likely many more. According to TrevE, the software is installed as a rootkit software in the RAM of devices where it resides. This software basically is completely hidden from view and in it virtually invisible, and worst of all, rather complicated to kill (some devices more so than others and you will see why in a few minutes). This is given root like rights over the device, which means that it can do everything it pleases and you will have nothing to say about it.

The whole security and privacy circus that started a few months back when researchers found out that the iPhone was sending location and other data to a central location has certainly woken up the interest of security experts world wide. The most recent cases as we have seen are holes in HTC's devices, all of which are bring addressed by HTC themselves with our help. However, there seem to be more than just devices doing this. As it turns out, and thanks to a tip from XDA member Fnorder, one of the most popular browsers for Android seems to be doing something similar as well. If you are a regular user of Dolphin, you have likely noticed the introduction of a new feature called webzines on this app. This feature basically is an aid to help the browser deliver content that may be of interest to you based on your usage patterns. Well, as it turns out, in order to do this, this service takes the liberty of sending every single piece of information that you access and search for on the browser to a certain location. No matter what you look for, all your search history and browsing history is stored somewhere.
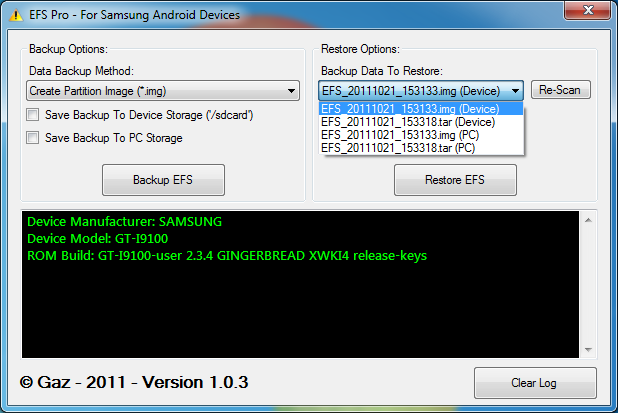
The wonderful world of NV, EFS, and all the inherent dangers that come from messing with this. For those of you who have no clue as to what I am talking about, there is a dark, really deep and well protected section of your device that is virtually immune to any kind of flashing and manipulation (unless of course you know how to access it). This part of the device contains information such as IMEI (or MEID and ESN in the case of CDMA devices), programming parameters for the device such as your account information (phone number, etc), data provisioning parameters, and a whole bunch of other things that, when not handled properly, can render a device completely useless. All of these are contained in the infamous \EFS folder. XDA Recognized Developer lyriquidperfection just updated an app that he started working on not too long ago, which basically allows you to back up and restore the contents of this folder, just in case. It seems to be rather simple to corrupt this by trying to unlock or change certain "numbers" in it, which is why being able to back up the original thing is rather important. HTC devices are normally associated with tweaking this due to the ease of getting the device in Diag mode via EPST. However, Samsung devices (and really most devices out there) can indeed be put in Diag mode to access this special section.

We all like to constantly flash our devices. Many roms support useful tools such as TitaniumBackup, Android MP, or even app2sd programs like Darktremor's, which will help us restore all of our programs even after a flash. There are many of us who like to keep the apks with us safely stored in a PC, but hate to install them or push them into the device one by one (particularly when the number of apps may be in the hundreds). If you fall within this small minority of Android users and would like to have a way to push all of these at once on your device, then you may want to look into what XDA member KarmaToBurn has prepared. Mass apk Installer will allow you to do just that. All you need to do is to place all your desired apps into a designated folder, and the script will take care of the rest. This will save you the work, but the time it takes for all of them to install will still be there. The good thing is that you will not have to be baby sitting your device throughout the whole thing.

