If you're big on security, you might have invested in home security through the likes of a Eufy camera. These cameras, while pricey, are special in that they promise to never store footage on remote, cloud-based servers, operating on a peer-to-peer basis unless you wish to pay for cloud storage separately. However, Paul Moore, a security researcher, has discovered that thumbnails and faces are being stored on Eufy servers. Eufy is a company owned by Anker.
Moore showed in a YouTube video how, even when his Eufy Homebase 2 is switched off, he can view a thumbnail from a camera recording that's stored on Eufy's servers. In the same way, faces can be seen as well that were identified in the footage, and those are also stored on AWS servers controlled by Eufy. These images appear to be deleted after 24 hours, but the fact remains that consumers such as Moore feel misled. Given that Eufy frequently states that privacy is the heart of its operation, it's understandable why Moore (and other consumers) would feel that way.
The below quote is taken from a Eufy product description on Amazon.
Your privacy is something that we value as much as you do. To start, we're taking every step imaginable to ensure your data private, with you. Whether it's your newborn crying for mom, or your victory dance after a game, your recorded footage will be kept private. Stored locally. With military-grade encryption. And transmitted to you, and only you. That's just the start of our commitment to protect you, your family, and your privacy.
Moore also demonstrated how these images are kept on these Eufy-controlled servers even after the footage is deleted. Even more alarmingly is that he talked about how it was possible to view a Real-Time Messaging Protocol (RTMP) stream from his camera without any authentication. He did not clarify if it was possible from an external network, or if someone would need to be on the same network as the camera to access this stream. He admittedly didn't show evidence of the feature, though said this was because of the potential danger of such a vulnerability being demonstrated publicly.
Making matters worse, Moore stated that videos were stored encrypted using a hardcoded security key of "ZXSecurity17Cam@", which he verified decrypted them locally. I found an unofficial GitHub repository for a Python library from 2019 for Eufy devices that makes reference to that same encryption key, suggesting that this is the case for multiple Eufy cameras that are out there.
Eufy responds
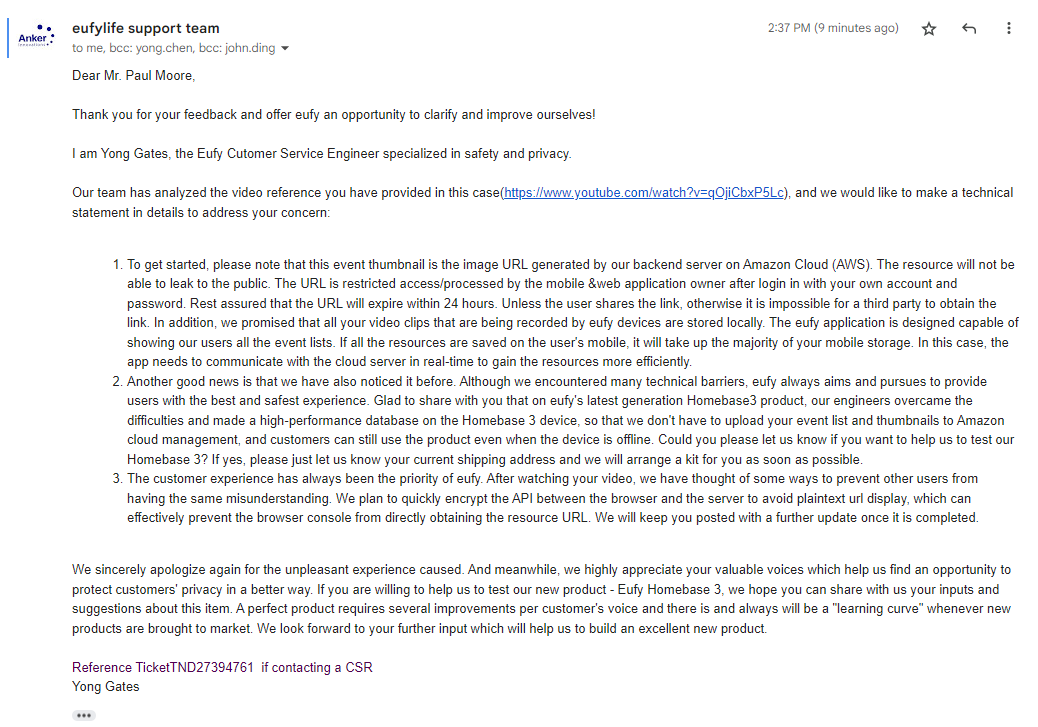
Moore had previously contacted Eufy and shared its response on Twitter. In the email, the company confirmed that it was storing these images on its servers, and pointed out the 24-hour expiration. The company said that it would add additional encryption to its APIs, and offered Moore the ability to test out its Homebase 3 device.
As for what all of this means, it's hard to make any overall judgments of the situation until it comes to a conclusion. We reached out to both sides of the conversation and so far have yet to hear back. We don't necessarily expect to hear back either, as Moore has said he has spoken to the company's legal department and will not be commenting any further currently.
What to do with your Eufy products
If you have Eufy products and are concerned from a privacy standpoint, it might be worth unplugging them to wait and see what happens next. It's unclear what exactly Eufy is doing, and without any further comments from those involved, it's hard to say to what degree consumers need to worry. It seems clear that many consumers feel misled, but to what degree isn't clear at the moment.
We'll be sure to update as this case drags on, and we expect that Eufy will release a statement in the near future in an attempt to allay concerns that consumers may have.