With each new version of Android, Google has increased its focus on security. Android 5.1 Lollipop added Factory Reset Protection as an anti-theft measure. Then, the company made encryption mandatory for high-performing devices since Android 6.0 Marshmallow. In Nougat, Google made the switch over to File-Based Encryption. Now, Google has detailed the Pixel 2's tamper-resistant hardware security module, which delivers "enterprise-grade security", according to the company.
The Pixel 2 and the Pixel 2 XL's hardware security module is a first for an Android device. It reinforces the lock screen against malware and hardware attacks. This is done in order to better safeguard the data stored on a user's device, which includes contacts, emails, photos, app data, etc. Google hopes that the Pixel 2 is the first of many Android devices that feature dedicated security modules.
We know that the lock screen is the first line of defence when it comes to protecting a user's data from attacks, as it is the point of vulnerability for brute force attacks. Google states that devices that ship with Android 7.0+ already verify a user's lock screen passcode in a secure environment, such as the Trusted Execution Environment (TEE).
This limits how often a malicious attacker can repeatedly try to guess it by brute-force. The key step is when the secure environment has successfully verified the user's passcode. Then, and only then it reveals a device and user-specific secret which is used to derive the disk encryption key, according to Google. The company states that without the disk encryption key, a user's data cannot be decrypted.
According to Google, the goal of these protections is to prevent attackers from decrypting user data without knowing the user's passcode. The company admits that the protections are only as strong as the secure environment that verifies the passcode - a weak link can compromise an entire security system even if every other component is secure.
This is where a hardware security module comes in. Google says that attackers will face more difficulty in attacking the device when it is performing "security-critical operations in tamper-resistant hardware".
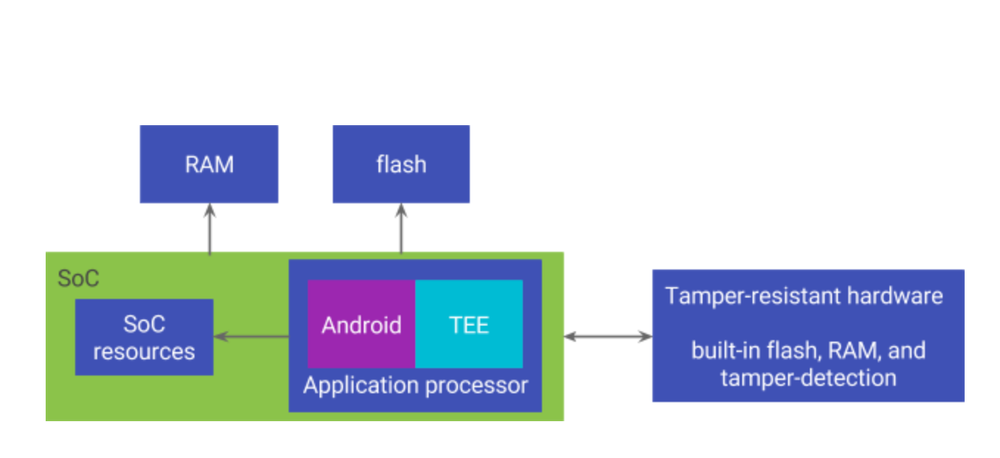
So what does a tamper-resistant hardware security module actually mean? In the Pixel 2, the tamper-resistant security module is in the form of a discrete chip, which is separate from the main SoC (the Qualcomm Snapdragon 835 in the Pixel 2's case). According to Google, the security module includes its own flash, RAM, processing unit, and other resources inside a single package. Therefore, it can control its own execution. This also helps it rebuff external attempts to tamper with it.
Google further states: "The package is resistant to physical penetration and designed to resist many side channel attacks, including power analysis, timing analysis, and electromagnetic sniffing. The hardware is also resilient against many physical fault injection techniques including attempts to run outside normal operating conditions, such as wrong voltage, wrong clock speed, or wrong temperature." Therefore, the tamper-resistant claim would seem to hold true on account of the above facts.
The Pixel 2's tamper-resistant hardware security module also helps to protect the device against software-only attacks. According to Google, it has an extremely small attack surface. This is because it performs very few functions, as it is dedicated hardware used for only specific purposes rather than being general-purpose hardware.
The key step in the process is that passcode verification occurs in the security module. Google states that even in the event of a full compromise elsewhere, the attacker cannot derive a user's disk encryption key without compromising the security module first - showing one of the major benefits of hardware security modules.
Google concludes by stating that the security module is designed in a such a manner that nobody - including Google itself - can update the passcode verification to a weakened version without having prior knowledge of the user's passcode.
For us, the blog post by Google was certainly illuminating. The hardware security module isn't a groundbreaking feature, but it reinforces the software protection that had existed before. Google did not identify the source of supply of the module, but XDA Senior Recognized Developer Dees_troy has stated that it was supplied by NXP. Already, there are concerns that security features like this may hinder development for the devices, showing that the battle between the focus on security and device development capabilities is still alive.