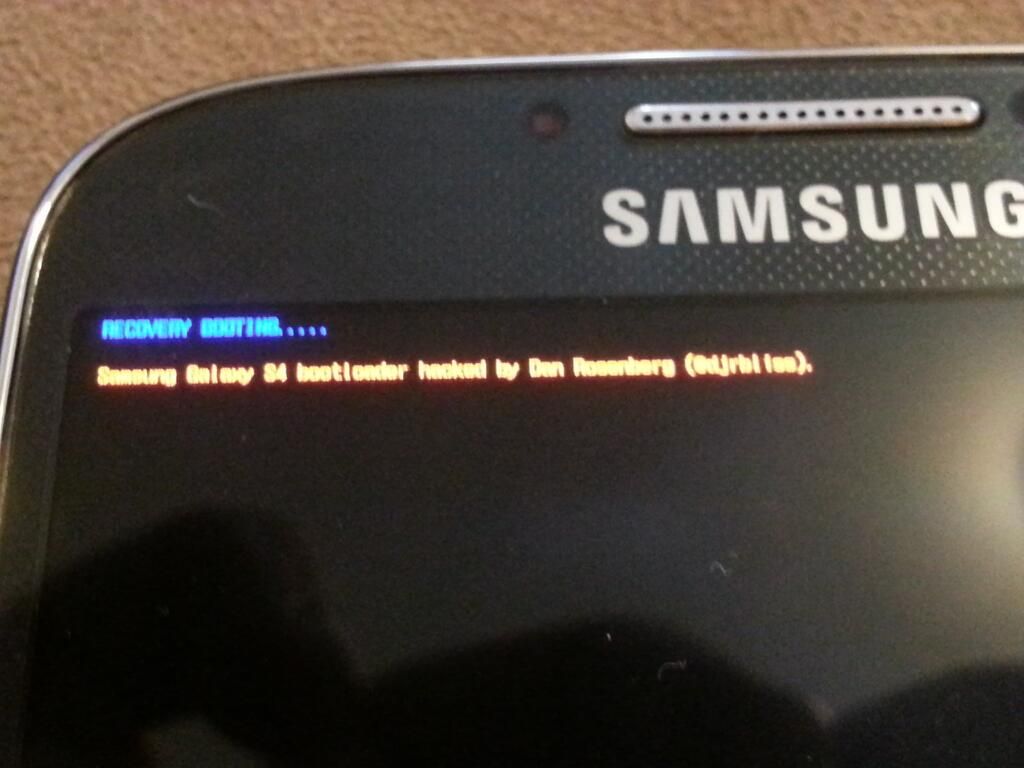
Dan Rosenberg has done it again... Well, he claims to have unlocked the Samsung Galaxy S 4 bootloader, giving only this slightly blurry image as proof. But anyone who's been paying attention will know that Dan, aka XDA Recognized Developer djrbliss, is good for his word.
The news comes via a set of Twitter posts over the last few days. The proof photo was posted about five hours ago, with zero details on how he did it. But if you hit his feed and look back a few posts, the picture becomes a little more clear. Two posts dated on April 29th give cryptic clues, literally. He mentions that RSA-2048 is used to sign the kernel and recovery. Looking at a quick Wikipedia reference on this key length tells us that this security is estimated to be uncrackable until at least the year 2030. So how the heck did he do it? Thus far, we know it was not due to a leak:
Is this the result of a leak?
No. I would not associate myself with the publication of confidential materials that are proprietary to these companies, regardless of the fact that I disagree with their policies on device openness. Plus, where's the fun in that?
Watch the XDA Portal for more news as this develops. And if you've got a tasty tidbit of information on this or other exploits use the "Tip Us" button on the top menu bar to help spread the word. To learn more from the source himself, visit the original thread.
Update: Thanks to Recognized Developer k0nane for the correction!