latest

Why home cybersecurity is important
Keeping yourself safe from online threats is more important than ever.
Our lives are more and more online than ever, and the wealth of security threats online is only increasing. It's important to protect yourself online, and with a few easy steps and some simple considerations, you can vastly decrease your chances of being exploited. We'll examine what features protect your home network from cybersecurity attacks, where some of the weak points are, and what you can do to ensure you're not one of the unfortunate few who are left picking their lives back up after being compromised.

Apple customers are being targeted by "MFA Bombing" password reset attack
A new report has highlighted recent MFA Bombing attacks against Apple customers, where the attacker also spoofs the company's support line.
Yesterday, we learned about the ZenHammer flaw in AMD hardware, which can lead to memory alterations. While this weakness can be difficult to exploit for the average attacker, malicious attempts to breach security don't always need to be highly technical. Such is the case with the latest "MFA Bombing" attacks that are currently targeting Apple customers.

Do you need an antivirus on Linux?
Antivirus software for Windows is big business, but do you need it if you're a Linux user?
Antiviruses on Windows have been big business for decades now, with an entire ecosystem of companies existing to protect Windows PCs. Microsoft even ships its own antivirus — Windows Defender — by default with Windows. But the question of whether you need an antivirus for Linux has been around for almost as long. There's a lot of nuance to this discussion, and the common claims that both viruses and antivirus software for Linux simply don't exist are false.

Microsoft disables MSIX protocol handler in Windows to thwart malware attacks
Microsoft has disabled the ms-appinstaller URI scheme handler by default in the latest version of App Installer due to a rise in cyberattacks.
The Windows AppX Installer spoofing vulnerability has been used by malicious actors for quite some time. Microsoft documented it as CVE-2021-43890 a couple of years ago. Back then, attackers were crafting packages containing ransomware that was distributed by exploiting this vulnerability, with Microsoft recommending customers to either install the latest version of the Installer or disable the ms-appinstaller protocol using Group Policy completely. Now, Microsoft has once again issued guidance regarding the vulnerability following a recent resurgence in its exploitation.
WinRAR has a major security vulnerability, manually update now
A WinRAR vulnerability is being widely exploited because the archiving utility does not allow automatically updating to a patched version.
WinRAR is one of the most used compression utilities out there, although Windows 11 might be looking to make a dent in its popularity with native support for 7Z, RAR, and TAR.GZ formats. However, those who leverage WinRAR may want to update the software as soon as possible as a security vulnerability is reportedly being exploited by certain state-sponsored actors.

This 26-course bundle will help you master cybersecurity for just $70, a 90% savings
A 26-course bundle that will help you learn the ins and outs of cybersecurity.
The internet can be a dangerous place, so being educated and vigilant is important. If you've ever thought about dabbling in cybersecurity, this bundle with 26-courses is going to be right up your alley. Normally, this bundle comes in priced at $754.99. But now, for a limited time, you can score this deal that knocks 90% off the regular price, and pick it up for just $70.

Gigabyte rolls out update to fix dangerous backdoor in its motherboards
Download and install the new firmware as soon as possible if your motherboard is affected by the vulnerability.
Gigabyte has released an update to fix a potentially dangerous security flaw in its motherboard firmware. The update is available on the official Gigabyte site for Intel 700/600/500/400 series and AMD 600/500/400 series motherboards. The company says it has conducted thorough testing and validation of the new BIOS before rolling it out to the public, meaning it should be safe to install right away. People with any of the affected motherboards should download the new firmware immediately to mitigate any risk.

Millions of Gigabyte motherboards were sold with a potentially dangerous backdoor
Hundreds of motherboard models with both Intel and AMD chipsets are affected, including the latest Z790 and X670 SKUs.
Cybersecurity research firm Eclypsium has discovered a potentially dangerous security flaw in the UEFI firmware of millions of Gigabyte motherboards. At least 271 models are said to contain the vulnerability, which could potentially open up a way for criminals to silently install malware on these systems under certain conditions. Both Intel and AMD motherboards from the past several years are affected, including many of the latest products with the Z790 and X670 chipsets.

Android OEM key leak means sideloaded "updates" could be hiding serious malware
Samsung, LG, and MediaTek are among the companies affected.
Read update
A crucial aspect of Android smartphone security is the application signing process. It's essentially a way to guarantee that any app updates are coming from the original developer, as the key used to sign applications should always be kept private. A number of these platform certificates from the likes of Samsung, MediaTek, LG, and Revoview appear to have leaked, and worse still, been used to sign malware. This was disclosed through the Android Partner Vulnerability Initiative (APVI) and only applies to app updates, not OTAs.

Cybersecurity is of utmost importance in today's day and age. For most companies, keeping their online infrastructure safe is a high priority. And for a behemoth like Google, the stakes are even higher. If you've ever wondered how the search giant defends its wide range of products and services against cyberattacks, you can now get an inside look with its new docuseries -- Hacking Google.

Your Wi-Fi devices may be vulnerable to FragAttacks
Belgian security researcher Mathy Vanhoef has discovered 12 new vulnerabilities, called FragAttacks, that affect almost all Wi-Fi devices.
At a time when Android OEMs are still in the process of rolling out patches to fix the Qualcomm modem vulnerability, Belgian security researcher Mathy Vanhoef has discovered 12 different vulnerabilities that impact most Wi-Fi-enabled devices. Vanhoef calls the collection of vulnerabilities "FragAttacks," and he claims that attackers can exploit them to access your data.

PSA: If you use ShareIt on Android, you should probably look for alternatives
Cybersecurity giant Trend Micro has discovered glaring security vulnerabilities in the ShareIt app on Android which put your sensitive data at risk.
If you're using the ShareIt app on your phone, you may want to uninstall it right away. Cybersecurity giant Trend Micro has discovered glaring security vulnerabilities in the file-sharing app that can be "abused to leak a user's sensitive data and execute arbitrary code with ShareIt permissions."

Android 11 Developer Preview: All the new Privacy and Security features
Google released the first Android 11 Developer Preview for the Pixel 2, 3, 3a, and 4. Here are all the new privacy and security features they announced.
Ahead of schedule, Google today released the first Developer Preview of the next version of the Android OS: Android 11. System images are available for the Pixel 2, Pixel 3, Pixel 3a, Pixel 4, but if you don't own one of these devices, you can also try out the Developer Preview via the Android Studio emulator or the Generic System Image. Although Google is saving most of the exciting new user and developer features for a grand announcement at Google I/O 2020, the company has shared a plethora of changes that are available in the first Developer Preview. Here's a summary of all the new privacy and security-related features that Google has announced in Android 11 Developer Preview 1.

[Update 2: Wi-Fi Easy Connect in Android Q] WPS disappeared in Android P and may never come back
WPS disappeared in Android Pie and has been marked deprecated, but it has a replacement in Android Q called Wi-Fi Easy Connect.
With Android P on the horizon, we're all excited to see what the final release brings us. We can expect to see performance improvements and new features like gesture navigation and a new UI. However, we can also expect a myriad of security enhancements, some of which may infuriate users at first. As first reported by AndroidPolice, it appears that Google may be deprecating WPS (Wi-Fi Protected Setup) support when Android P releases. For those who aren't aware, WPS allows you to connect a device to your router simply by pressing a designated button on your router. Some configurations then require you to enter a PIN code on your device.
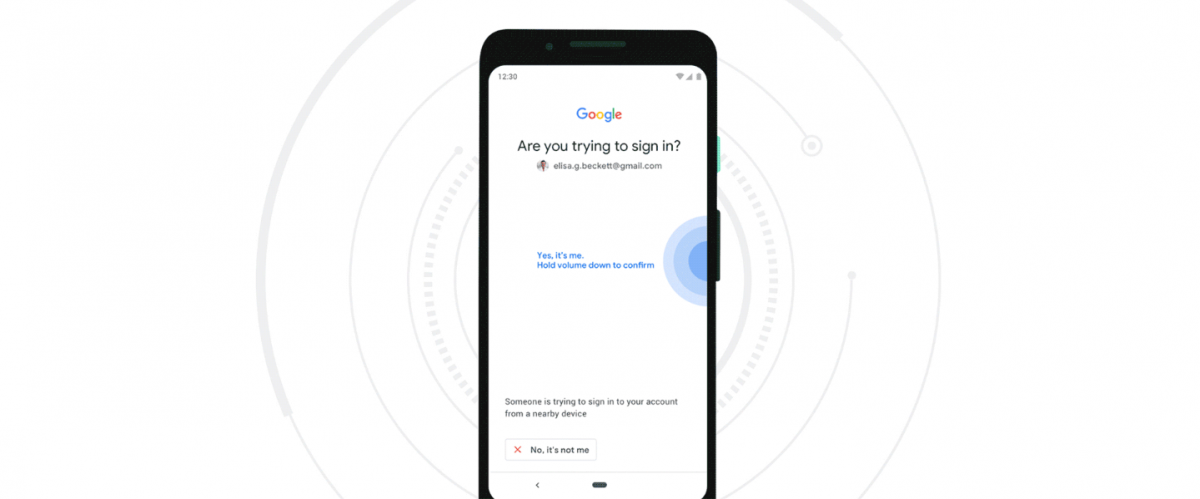
Android 7.0+ phones can now be used as 2SV security keys for Google accounts
Google has announced that smartphones with Android 7 and above can now be used as Two Step Verification (2SV) physical security keys for Google accounts.
With every passing day, we spend more of our time building our online identity. These online identities have become absolutely tied into our physical lives, making them very lucrative targets for people with impure motives. So it comes as no surprise that phishing attacks are one of the most common causes of security breaches, as attackers trick and steal these online identities to cause major damage. Two-step verification a.k.a. 2SV makes it difficult to steal online identities, and physical 2SV security keys, like the Titan Security Key from Google, are considered to be the strongest and most phishing-resistant method of 2SV as they ensure your physical presence when accessing these online identities

[Update 3: It's Dead] Google+ is shutting down for consumers after potential major data breach
After a massive data breach that reportedly affected over 500,000 users, Google is set to shut down the consumer version of Google+ for good.
Google+ was introduced in 2011 as the tech giant's response to the rising social network phenomenon and as a rival to Facebook, Twitter, and other social networks. Unfortunately, though, it failed to gain traction despite Google's unmeasurable efforts and backing to bring it up and boost its adoption. Today, after over 7 years of existence, Google is shutting down Google+ for good--although its low user base surprisingly wasn't the main factor behind this decision.

Google announces Chrome Web Store changes to protect you from malicious extensions
Google is announcing several changes to make extensions more secure in the Chrome Web Store. These changes will be rolling out soon.
Google is making some changes to better protect Chrome users from malicious extensions. Recently, Google has been working to make Chrome extensions safer. They no longer allow users to install extensions from outside the Chrome Web Store and they removed extensions that were using cryptocurrency mining scripts. Today, they are announcing even more changes.

US Senator pushes government to stop using old VPN tech and use WireGuard
US Senator Ron Wyden wrote an open letter to NIST to discourage use of older VPN tech like OpenVPN and IPsec, and use WireGuard instead.
VPNs have played a pivotal role in today's age, allowing users to bypass geographical restrictions and keep their data relatively secure from prying eyes. While the use of a VPN is recommended against not using one at all when dealing with important information, some of the most popular VPNs have their own set of problems that make them a flawed choice despite their popularity.

Every Android device is susceptible to a hardware vulnerability called RAMpage
Every Android device is susceptible to a hardware vulnerability called RAMpage. You can read all about it here, and how to test your own Android device.
We have consistently seen various vectors of attack rear their head when it comes to Android smartphones. We've seen Shattered Trust, Cloak and Dagger, and Rowhammer, just to name a few. RAMpage is the latest one on the block, and while it is a hardware vulnerability, it doesn't necessarily need physical access to your device to exploit. How it works is relatively simple.

WPA3 WiFi security standard is final & coming to devices with the Snapdragon 845
The WPA3 WiFi Security standard has been certified, and will be coming to devices powered by the Qualcomm Snapdragon 845 in the future.
The WPA3 WiFi security standard has been certified, as announced by the Wi-Fi Alliance earlier today. It's yet another incremental network security protocol upgrade and was necessary after WPA2 was cracked wide open early last year - eleven years after it was officially unveiled. Devices require more enhanced security hardware to utilize it, something which the Qualcomm Snapdragon 845 can provide once OEMs roll out support to their devices.









