latest

Your Wi-Fi devices may be vulnerable to FragAttacks
Belgian security researcher Mathy Vanhoef has discovered 12 new vulnerabilities, called FragAttacks, that affect almost all Wi-Fi devices.
At a time when Android OEMs are still in the process of rolling out patches to fix the Qualcomm modem vulnerability, Belgian security researcher Mathy Vanhoef has discovered 12 different vulnerabilities that impact most Wi-Fi-enabled devices. Vanhoef calls the collection of vulnerabilities "FragAttacks," and he claims that attackers can exploit them to access your data.
Qualcomm modem flaw affects 30% of all phones; lets attackers record phone calls
Security researchers have discovered a new flaw in Qualcomm's Mobile Station Modem that affects around 30% of all Android phones.
Israeli security firm Check Point Research has discovered a flaw in Qualcomm's Mobile Station Modem that affects millions of Android phones worldwide. The firm claims that hackers can exploit the vulnerability and gain access to your text messages, phone calls and, in some cases, even unlock your SIM card.

Here's why you should be wary of installing anything that sets SELinux to permissive
An undocumented Android feature allows any arbitrary app to gain root access on a permissive SELinux environment. Read on to know more!
In the world of Android modding, people tend to regard root access as the cornerstone of all things. It allows users to take complete control of their devices and add features that aren't always available in the stock configuration. But as they say — "with great power comes great responsibility" — it's not wise to bypass Android's security model unless you know what you're getting into. For veteran Android enthusiasts on our forums, you are probably aware of the potential for backdoors to exist on your device, and you are more likely to be running a trusted root-enabled mod on top of the latest Android version with the latest security patches. Having said that, you might know a few people who don’t really care about what root tweaks they install so long as they seemingly work for them. This is why you can still find a truckload of mods that only work when SELinux is set to permissive, which, in turn, leave their users extremely susceptible to security threats.

StrandHogg 2.0 Exploit Explained - Why Users and Android App Developers should care
StrandHogg 2.0 is a dangerous new Android vulnerability. Here's how it can affect users and how developers can protect their apps against it.
It's 10:00 PM. Do you know where your Activities are? There's a new vulnerability that can be exploited on millions of Android devices, and it's a pretty nasty one, too. In a nutshell, this design flaw allows an attacker to present their own Activity (page) on top of another app's, potentially confusing the user into giving away their private data. The vulnerability has been dubbed StrandHogg 2.0 and was recently disclosed by Promon, a Norwegian security firm.

How Monthly Android Security Patch Updates Work
Ever wondered how the monthly Android security patch updates work? Wonder no more, as we've got just the primer for you to understand the entire process.
Google has been publishing monthly security bulletins since August of 2015. These security bulletins contain a list of disclosed security vulnerabilities that have been fixed which affect the Android framework, Linux kernel, and other closed-source vendor components. Every vulnerability in the bulletins was either discovered by Google or disclosed to the company. Every vulnerability listed has a Common Vulnerabilities and Exposures (CVE) number, along with associated references, the type of vulnerability, a severity assessment, and the AOSP version affected (if applicable). But despite the seemingly simplistic process behind how Android security patches work, there's actually a somewhat complicated back-and-forth behind the scenes that allows for your phone to get monthly or (hopefully) near-monthly patches.

Critical MediaTek rootkit affecting millions of Android devices has been out in the open for months
A critical flaw in MediaTek processors went unpatched in devices due to OEM neglect. Google hopes the March 2020 Android Security Bulletin will fix this.
On the first Monday of every month, Google publishes the Android Security Bulletin, a page that discloses all the security vulnerabilities and their patches submitted by Google themselves or other third-parties. Today was no exception: Google just made public the Android Security Bulletin for March 2020. One of the vulnerabilities that are documented in the latest bulletin is CVE-2020-0069, a critical security exploit, specifically a rootkit, that affects millions of devices with chipsets from MediaTek, the large Taiwanese chip design company. Although the March 2020 Android Security Bulletin is seemingly the first time that CVE-2020-0069 has been publicly disclosed, details of the exploit have actually been sitting openly on the Internet—more specifically, on the XDA-Developers forums—since April of 2019. Despite MediaTek making a patch available a month after discovery, the vulnerability is still exploitable on dozens of device models. Even worse, the vulnerability is actively being exploited by hackers. Now MediaTek has turned to Google to close this patch gap and secure millions of devices against this critical security exploit.

Google Camera and Samsung Camera apps exposed camera and video intents to third-party apps
Google Camera and the Samsung Camera apps exposed their Camera and Video intents to third party apps, giving rise to a permission bypass vulnerability.
When compared to iOS, Android provides applications a lot of ways to interact with each other, enabling developers to build some of the more common Android features we have come to expect and love. This is made possible thanks to Android's Intent system, which allows any app to send any intent it wants, and allows receiver apps to handle these intents in creative manners. But as it turns out, the Google Camera app and the Samsung Camera app have left their camera and video intents exposed to third-party apps, which leaves the door open for potential misuse by bypassing critical permissions, as demonstrated by the security researchers at Checkmarx.
[Update: Patched] Actively exploited zero-day vulnerability found in Google Pixel, Huawei, Xiaomi, Samsung, and other devices
Researchers at Project Zero have found an actively exploited zero-day security vulnerability that compromises Google Pixel devices and others! Read on!
Security has been one of the top priorities in recent Android updates, with improvements and changes to encryption, permissions, and privacy-related handling being some of the headlining features. Other initiatives such as Project Mainline for Android 10 aim at speeding up security updates in order to make Android devices safer. Google has also been diligent and punctual with security patches, and while these efforts are commendable in their own right, there will always remain scope for exploits and vulnerabilities in an OS like Android. As it turns out, attackers have been allegedly found actively exploiting a zero-day vulnerability in Android that allows them to take over full control of certain phones from Google, Huawei, Xiaomi, Samsung and others.

[Update: Fix Rolling Out] ES File Explorer vulnerability allows an attacker on the same network to grab any file from your phone, but it'll be fixed
A vulnerability in ES File Explorer allows an attacker on the same network to steal any file from your device. It will be fixed.
ES File Explorer was once touted as the file explorer to beat before being bought out by Cheetah Mobile. The application quickly became inundated with advertisements, but those with premium versions of the application may have continued to use it. Even now, I know people who still use the free version of the application, citing the fact that it "just works." That's despite the fact that there are many alternatives that are also just better across the board. MiXplorer, FX File Explorer, and Solid Explorer, just to name a few. Now it turns out that anyone using ES File Explorer can have any file stolen from their device remotely by somebody on the same network. The vulnerability was reported by French security researcher Baptiste Robert, who goes by the online pseudonym "Elliot Alderson" - a reference to the protagonist of the TV show Mr. Robot.

Millions of users' data leaked through misconfigured Firebase backends
Millions of users' data have leaked through misconfigured Firebase backends, leaving plaintext passwords and more publicly viewable.
Millions of users' data have been leaked because of misconfigured Firebase backends, according to a report from Appthority. Around 113GB of data over 2,271 databases were exposed publicly as a result of being misconfigured. Firebase is a Backend-as-a-Service offering by Google which was reported to be the fastest growing SDK in 2017. The service is hugely popular among the top Android developers. It provides cloud messaging, push notifications, databases, analytics, advertising and a lot more that developers can utilize, all powered by Google's high-performance servers. However, it seems that many developers are misusing it.

LineageOS Introduces "Trust" - A Centralized Interface for Security and Privacy
The developers over at LineageOS have introduced Trust: a centralized interface for security and privacy features in the ROM. Read on to know more!
The introduction of monthly security patches for Android was a welcome and much-needed move from Google. At that time, Android was infamous for its fragmentation issues, which negatively impacted how security vulnerabilities could be patched and then quickly distributed to devices. Monthly security patches provided a quick way for concerned users to judge how "secure" and "up-to-date" their device really was.

[Update: Fix] Bootloader Protection Bypass Discovered on OnePlus 6 (requires physical access)
A serious vulnerability in the OnePlus 6 bootloader has been discovered. This exploit, which requires physical access, bypasses all security measures.
The OnePlus 6 was made official in the middle of last month. The device has only recently started to make its way into the hands of consumers and developers on our forums, and already we're hearing about the work that's being done. An official build of TWRP is already available and work is progressing nicely on an unofficial LineageOS 15.1 GSI. The OnePlus 6 isn't only receiving attention from users interested in the device for their personal use or projects, however, as security researchers are starting to take a closer look at the device to see what they can find.
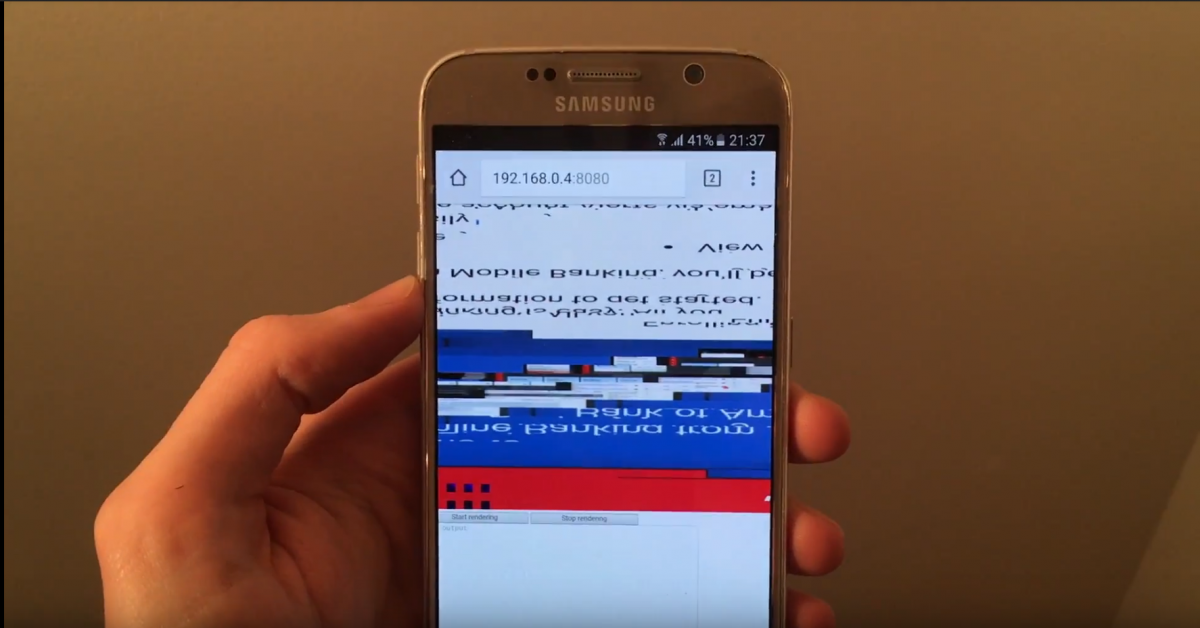
How a graphics driver bug on the Samsung Galaxy S6 leaked Google Chrome tab data
Ever wonder how security vulnerabilities are found? UK based firm GraphicsFuzz explains how they came across a graphics driver bug on the Samsung Galaxy S6 that they could exploit to see data from opened tabs in Google Chrome.
Back in late March, a U.K. based start-up firm specializing in testing GPU reliability approached us with a GPU bug they discovered that causes the Qualcomm Snapdragon 845 Samsung Galaxy S9/S9+ to reboot when visiting a web page. The firm, called GraphicsFuzz, worked with us to report the issue to Qualcomm and Samsung. Some of our readers were interested in learning just how a company like GraphicsFuzz is able to find these vulnerabilities, so we collaborated with the company to showcase how they discovered an older GPU vulnerability. This already-patched vulnerability allowed an attacker to remotely "spy" on the contents of Google Chrome browser tabs on the Samsung Galaxy S6.
Password Managers using Android Oreo's Autofill API are Potentially Vulnerable to Data Leakage
A potential security flaw in Android Oreo's Autofill API allows for password managers to leak data such as passwords, addresses, or credit cards.
Autofill is one of the biggest, and most publicized new features introduced with the release of Android 8.0 Oreo. Many different password managing apps, like LastPass, have already implemented this new API into their applications. And while it can prove to be quite the improvement over the previous Autofill implementations using Accessibility Services, there's a potential security flaw to consider. Last month, a white paper was published to GitHub, documenting an inherent flaw in the Android Oreo Autofill API that could potentially lead to your password manager leaking more of your personal data than you gave it permission for. We're going to do a quick rundown of the white paper written by Mark Murphy (better known as CommonsWare) and published on his GitHub page on August 8th, 2017.






