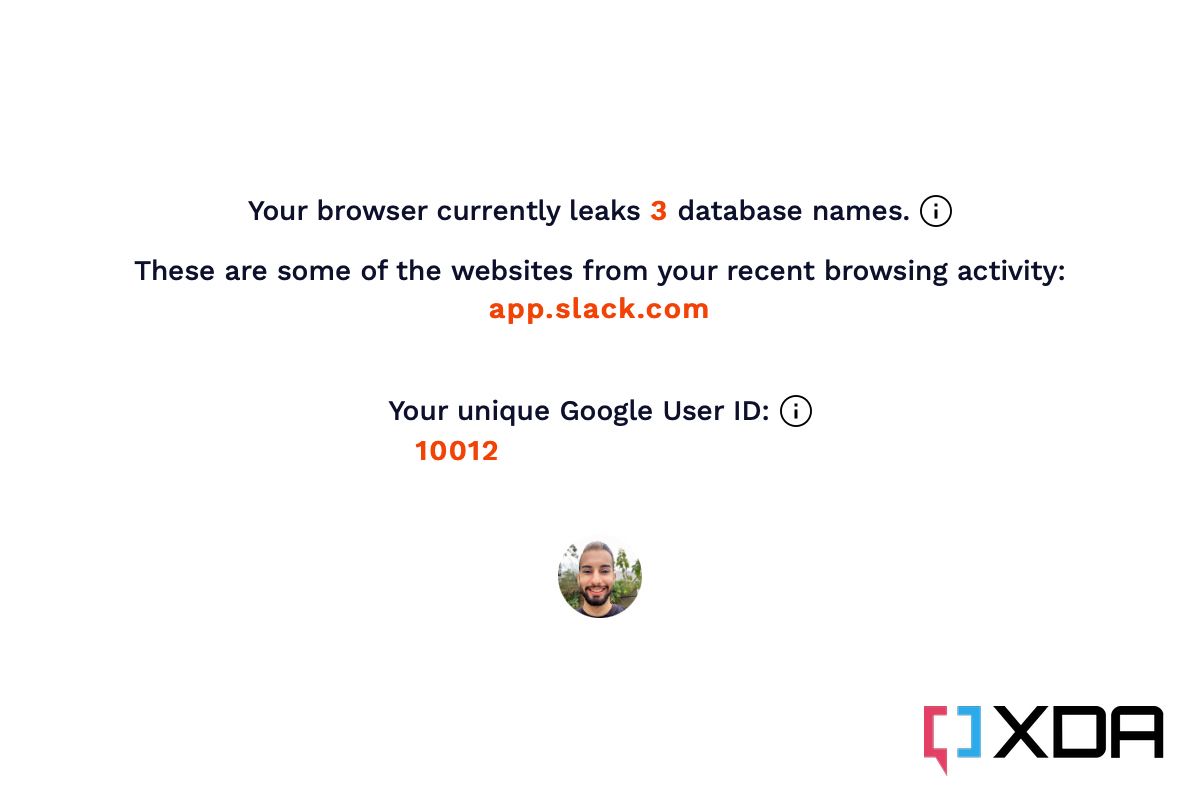
Apple markets itself as a privacy-focused corporation, but no internet-connected device is truly secure. And despite its claims, the company sometimes takes a long time to patch reported exploits. The latest report highlights that malicious websites can access some of users' Google account details and recent browsing history on Safari. The exploit was shared with Apple back in November, and it still hasn't been resolved.
FingerprintJS has disclosed this serious Safari bug in a recent blog post (via 9to5Mac). Safari's IndexedDB implementation on Apple's operating systems allows websites to read other domains' database names. While this implementation doesn't grant them access to the actual contents of the databases, the names themselves can reveal a lot about a user. For example, Google stores the data of logged-in accounts using users' unique IDs as database names. This enables a website to access even more of your information, as the Google User ID is used to make Google services API requests. The fix to this bug would be restricting websites from viewing other domains' database names. FingerprintJS further explains:
Note that these leaks do not require any specific user action. A tab or window that runs in the background and continually queries the IndexedDB API for available databases, can learn what other websites a user visits in real-time. Alternatively, websites can open any website in an iframe or popup window in order to trigger an IndexedDB-based leak for that specific site.
Considering the seriousness of this bug, it's unclear why Apple hasn't patched it yet. With the exploit getting published publicly, we can only hope that the company patches it in an upcoming build of iOS 15.3. In the meantime, if you're on macOS, you can protect yourself by switching to another web browser. Unfortunately, though, all browsers on iOS and iPadOS are affected, as they're based on Apple's WebKit.
Which web browser do you primarily use, and why? Let us know in the comments section below.